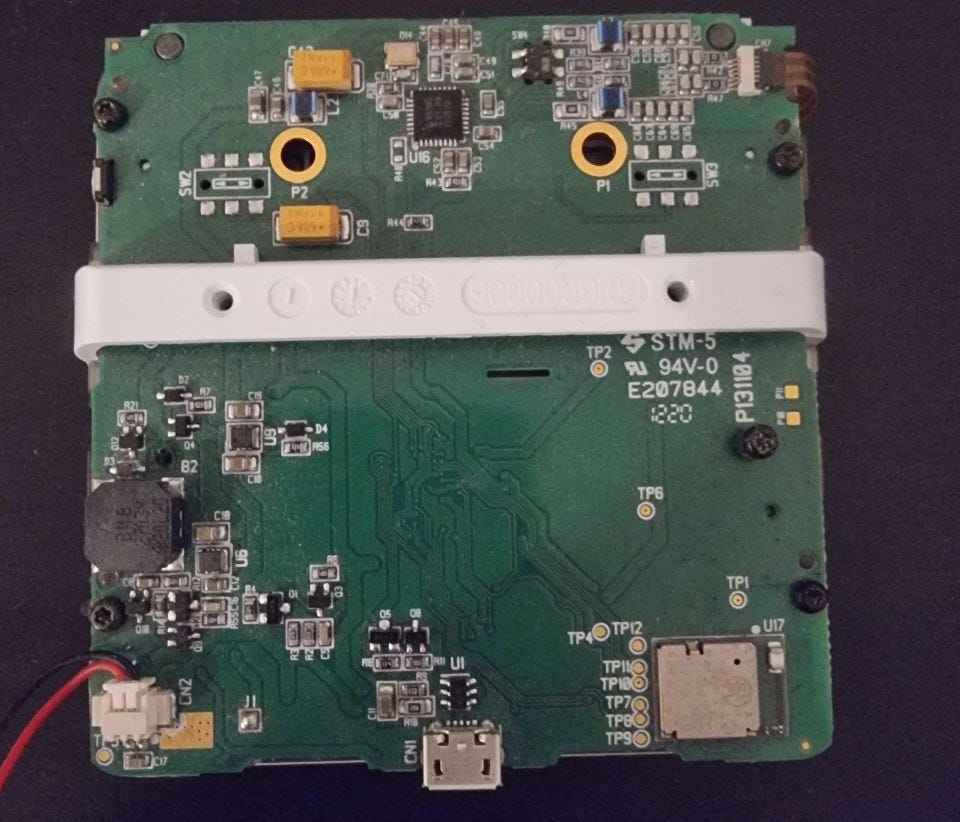
About a year ago I walked through a German consumer electronics store and got absolutely nerdsniped. Right next to usual consumer electronics, think cameras, laptops and keyboards, I saw this:
A card terminal that I can just buy off the shelf?!
You may ask yourself, why am I so shocked about card terminals being sold in a store?
This is because card terminals, and more generally Point-of-Sale products are renowned clandestine pieces of hardware.
They are generally equipped with systems which recognize tampering, e.g. opening their case, and then proceed to self-destruct. Don’t worry they won’t explode, but instead they delete all necessary keys and certificates and turn into a paperweight with a display and pin pad.
So naturally I bought three of them at approximately 40 euros per piece, and euphorically went home.
I proceeded to brick my first one, look at the tamper detection methods and reverse engineered the companion Android app with Frida.
After the initial joy weared off, my 120€ investment forced me to perform more in-depth research into the topic of card payments.
But this post isn’t about how I hacked this device, installed my custom firmware, played Doom on it and stole millions, the suspense arc is a lot flatter than I hoped for.
What’s skimming about?
Skimming describes the act of obtaining details from credit or debit cards, usually with the goal of creating a clone of that card. A clone of a card, especially a credit card, opens the door to steal a lot of money.
Folks living in countries like the US may be familiar with skimming, from news stories about manipulated ATM’s, gas station card terminals etc.
Consumers swipe their card somewhere, and weeks later they are confronted with an empty bank account, or even worse huge debt on their credit card.
Now as a German, I only know skimming because I read KrebsOnSecurity since I am 11 years old. These nerve wracking stories about groups building complex devices such as deep-insert skimmers, getting hunted through the country by security enthuasiasts with Bluetooth signals always hit a sweet spot for me.
A very simplified overview for these devices sounds like this:
Old cards (or also new cards in some countries) have magnetic stripe, which stores data.
This data is organized into Tracks, typically Track 1 and Track 2, think of it like a .txt file with line breaks.
The data encoded in these magnetic stripes consists of the Name of the card holder, the account number, expiry dates and some other magic values, available here.
But all in all: This data is purely static. Think of it like a password, like your credit card number, expiry date and CVC code you need to enter to pay something online.
This also means: If you manage to read that card, you can clone that card 1-to-1, and the PoS terminals can’t tell the difference between the original and your cloned card.
The aforementioned skimming devices usually consist of a magnetic card reader, which “man-in-the-middles” the original equipments magnetic card reader, creating a silent carbon copy of the presented card.
Normally additional security measures are added with these magstripe cards, such as a PIN. But this PIN mechanism is implemented on the banks side, and not connected to the actual, physical card.
So if these skimmers have a camera attached, which records the PIN pad, you have the cloned card, and the PIN, nobody can tell the difference between you and the person who has been issued the original card.
This crime also works by infecting PoS systems with malware, and intercepting the Track data and PIN, which often enough is just plaintext written to RAM.
Who is EMV?
EMV stands for Europay, Mastercard and Visa. These three competitors are issuing cards for banks, and teamed up to defeat their common enemy: Credit card fraud.
They have written a standard, which forces implementors (like SumUp) to use a specific protocol and adhere to their security guidelines. If they don’t, your card terminal won’t accept Europay, Mastercard or Visa.
My device-under-test, the SumUp Air, is what PCI calls a Pin Entry Device.
The PCI has a list of security requirements, which is normally under NDA but the test-report containing all requirements verbatim is public.
The requirements range from straight-forward ones like “the different numbers on the PIN pad shall make the same sound, so that an attacker can’t hear the PIN sequence” to “the device shall have tamper-detection, which detects intrusion by milling, chemical solvents etc. which triggers the device being unusable for payment transfers”. So we finally know why these devices self-destruct!
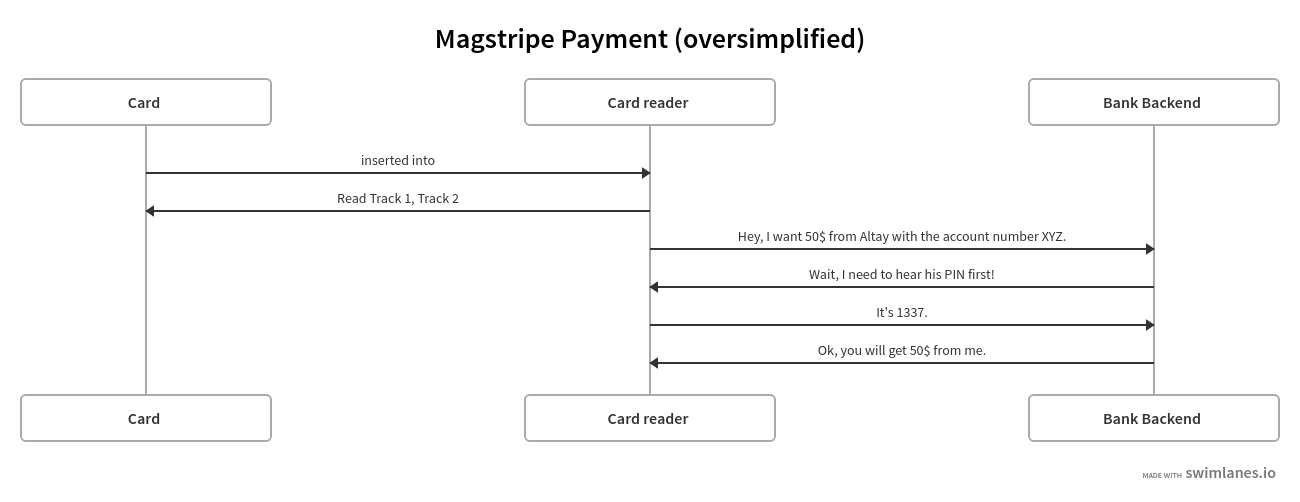
EMV vs traditional Magstripe
To understand why skimming Magstripe devices works, read through this sequence diagram.
Notice how the card is only there to give the Track 1 and Track 2 data?
If the Track data and PIN is intercepted once, anyone with access to the Bank’s backend (or a payment provider or whatever) can successfully fool the systems, that the person whose funds he wants to steal is standing in front of him.
With a card in his hands and his PIN in his mind.
Enter the crypto enclave
Crypto enclaves are a common concept, and you most likely have multiple of them in your pockets right now.
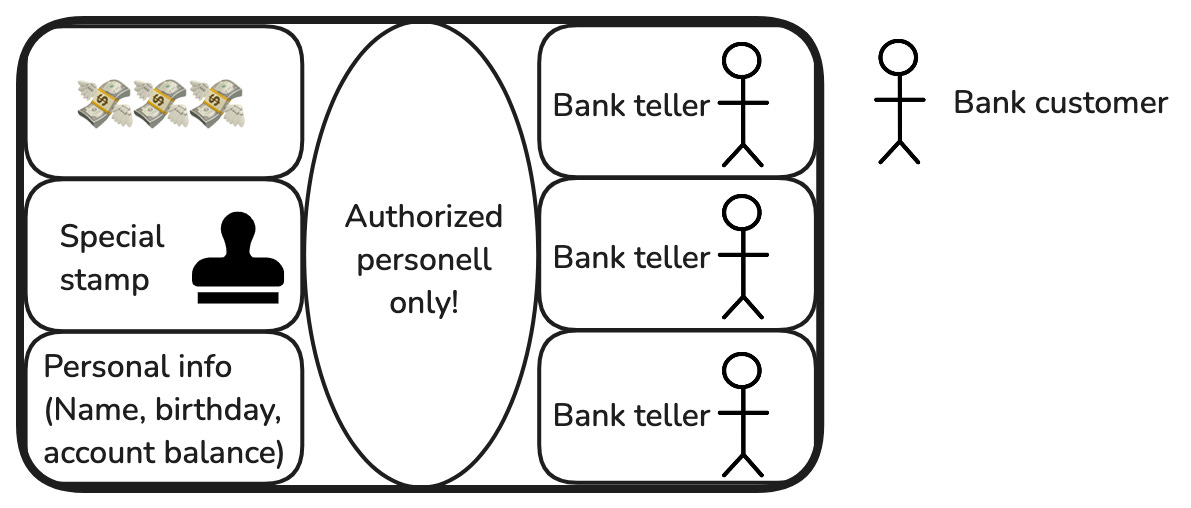
Try to think of it like this:
You go into a bank to e.g. write a huge check. You approach a bank tellers cabin, behind bulletproof glass.
You ask him to give you a check of 30k for this and that, he checks if you are really the person who owns the bank account.
If he is successful in doing so, he gives you a piece of stamped paper with the number of 30k written onto it.
Just because you showed up once, and proved that you are in fact who you are claiming to be, you cannot give out arbitrary checks. Only the bank teller can leave his cabin, get the special stamp, and stamp your check so it is actually a check, and not a piece of paper.
(I don’t know if checks really work like that, we don’t really use them in Germany)
And a crypto enclave is just that, but the office is a piece of software, and the Bank teller is an API.
The chip in your SIM card, in your bank card or any other smart card is a fully flegded computer, which runs an application with well defined interfaces.
Seriously, just Google SIM Card pinout, it has a power supply, Ground and Data transmit/receive pins. The app is funnily enough typically a Java Applet, back when the JVM was thought to be the standard in embedded development.
The interfaces on that card are defined by the EMV protocol.
This is how your payment looks like with EMV:
Notice how the card is kept in the loop? The card is proving it’s physical presence at the card reader by it’s possession of the secret stamp. This secret stamp is never leaving this card, even if you enter the PIN, best you’ll get it is an autograph.
This is why EMV is commonly called Chip and PIN!
Signature deep-dive
Feel very free to skip this part
Now the chip doesn’t really hold a stamp in it’s tiny package, and also stamps can be cloned easily, especially if you look at the sophistication of those aforementioned skimming groups.
When the card terminal asks the card for money, and provides a valid PIN, a cryptogram is generated, the ARQC.
The card gathers the data for the transaction, like the Transaction amount, currency, a random number (provided by the Card reader), and a Transaction counter (more on that later). It then encrypts this data with 3DES or AES, using his private key.
This private key isn’t static, in reality a temporary session key (SKAC) is generated by a “core” Application Cryptogram Master Key (ACMK) and the aforementioned Transaction counter. The ACMK is static, and is also known to the bank who issued his card, so a pre-shared key.
If the card reader says: “Altay Akkus says he wants to give me 50$”, the bank will calculate this ARQC locally, and ask the card reader for the ARCQ of the card, and if these match, the bank can be sure that the card with Chip and PIN were present at that card reader.
If you want to see a more in-depth explanation of this Cryptogram, check out this article.
Ok but what about i++?
While I was aware of the fact that EMV used cryptographic signatures for transactions, I wasn’t fully aware of consequences.
Think of these attack scenarios:
Mallory buys a SumUp Air and manages to install malware onto this terminal. He has fully compromised that terminal, he can do whatever he wants.
Mallory sells that SumUp Air on eBay “as good as new” to an unsuspecting small business owner who wants to save a few bucks.
Attack scenario 1: Steal the PIN
Mallory logs the PIN that was entered, and sends it to his Command-and-Control server.
First off, EMVs interfaces don’t tell you the name or IBAN of the card that you are reading. So trying to scam your way into online banking (most users with a card PIN of xyzw use an online banking 6-digit PIN of xyzwxy) will not work.
Second off, remember it’s chip AND PIN, just the PIN will not get you far.
Attack scenario 2: Show 50$, pay 150$
This works, but your customer will call the bank as soon as he realizes.
Attack scenario 3: Create the legit transaction first, illicit transaction second.
You can do this, you can make the terminal work like normal, and then request a second check/signature. You just need the card being present, and the PIN, so you can create as many transactions as you like too.
You could even use that signature to withdraw money on these fancy new contactless ATMs.
But if you have not read the deep-dive: The stamp which is used changes it’s color after each transaction.
Each time your card generates a check, it increments a local counter by 1. And each time your bank gets a check from your card, it also increments a local counter by 1.
Let’s say the sequence of colors is Red, Black, Green, Orange.
You pay at store #1, everything is fine, your bank gets a red stamp, and approves that transaction.
Now you go to store #2, where the tampered card terminal is installed, and your card generates the first, real, transaction with black ink. But because that card terminal is naughty, it requests a second transaction of 10k.
The card is being presented the right PIN, so it gives you a check with green ink.
Note that the bank expects that the next check it is going to receive from your card is going to stamped with green ink. You have to cash that transaction immediately.
Let’s say Mallory keeps that second, fraudulent transaction for a few days so grass can grow over it.
When the victim goes to the next store to buy something, the card is going to stamp the next check with orange ink.
If Mallory did not submit that fraudulent transaction before you pay your next bill with your card, the bank will expect green ink, but will instead get orange ink.
And this is going to cause a lot of trouble on the banks side.
When they start looking into the issue, why this card is misbehaving, they will see that everything ran smooth until the customer visited the shop of that aforementioned small business owner with the tampered card terminal.
This will lead to the business getting some unpleasant visitors, namely the local police department.
And even if Mallory cashes in the second check directly after the first one, the victim will contact his bank and claim that the ATM withdrawal in Munich 5 seconds after he bought something in Berlin was not made by him.
And then, once again, the business will get some unpleasant visitors.
So Mallory can’t collect valid checks for weeks, or even months, and then claim them all in one big sweep and get rich off it.
His cover will be blown after the first transaction, and there will be an indisputable trail of evidence leading back to his tampered EMV terminal.
Even if I were to show that these can be fully compromised, it would not really help any attacker to realize financial gains from this hack.
And that, dear folks, was not in my mind when I spend 120€ on those terminals.
In Germany we call this “Lehrgeld”, “education money”, and I certainly learned a thing or two about the payment industry.
This is Grade A security by design, kudos to Europay, Mastercard and VISA and all others who work so my money stays mine!
PS: Strangely enough, this was oddly similar to Rolling codes in car key fobs, which I have extensively worked with before.
The giant advantage that these cards have over keyfobs is that “checks” cannot be lost in transit, so you don’t have to resynchronize these counters once in a while like cars do.
E.g. because your kids pressed the key many times without the car being near-enough to hear it, so the counter of your fob and key “run away” from each other. Most attacks on newer cars work by exploiting this disadvantage.
PPS: I know EMV also supports offline cryptograms, but the card can decline serving offline-transactions, which they typically do, especially when a lot of money is involved. This is why your card sometimes asks for your PIN, and sometimes doesn’t, by the way!